A fun small project I worked on earlier this year was creating an HTTPS Everywhere custom ruleset channel for the SecureDrop project. HTTPS Everywhere is a popular browser extension maintained by EFF that rewrites HTTP URLs to HTTPS when possible. A set of rules is used to determine how URLs should be rewritten. HTTPS Everywhere is included in Tor Browser to reduce the impact of malicious exit nodes.
This is relevant for SecureDrop, because each news organization advertises an onion URL that corresponds to the web application (“source interface”) where a source should upload documents. These URLs are not human readable: an example URL v2 onion services is yyhws9optuwiwsns.onion. With v3 onion services, they are even longer: l5satjgud6gucryazcyvyvhuxhr74u6ygigiuyixe3a6ysis67ororad.onion.
The HTTPS Everywhere folks suggested that we could use the custom ruleset functionality in HTTPS Everywhere to create a list of rules rewriting human-readable names to the onion URLs for SecureDrop source interface. This can be scoped to a namespace such that this custom ruleset can only rewrite URLs that end in e.g. securedrop.tor.onion.
Here’s a little gif showing the rewriting:
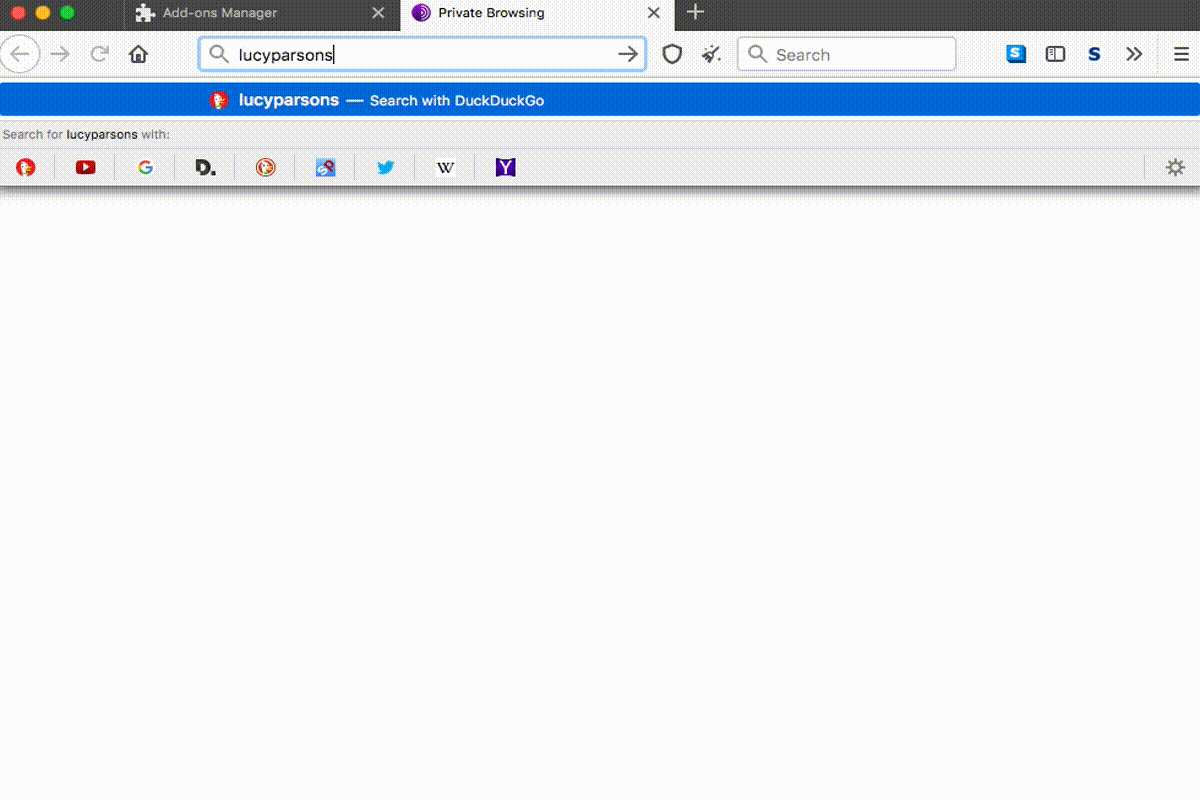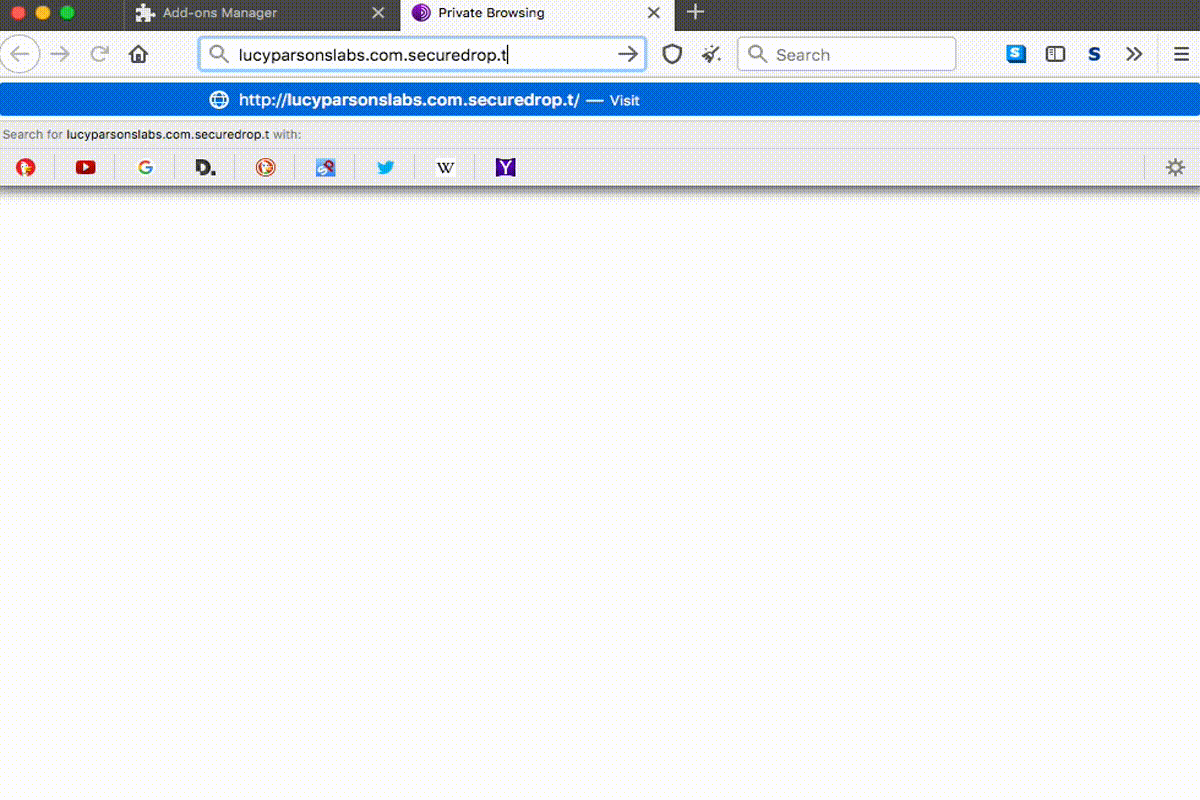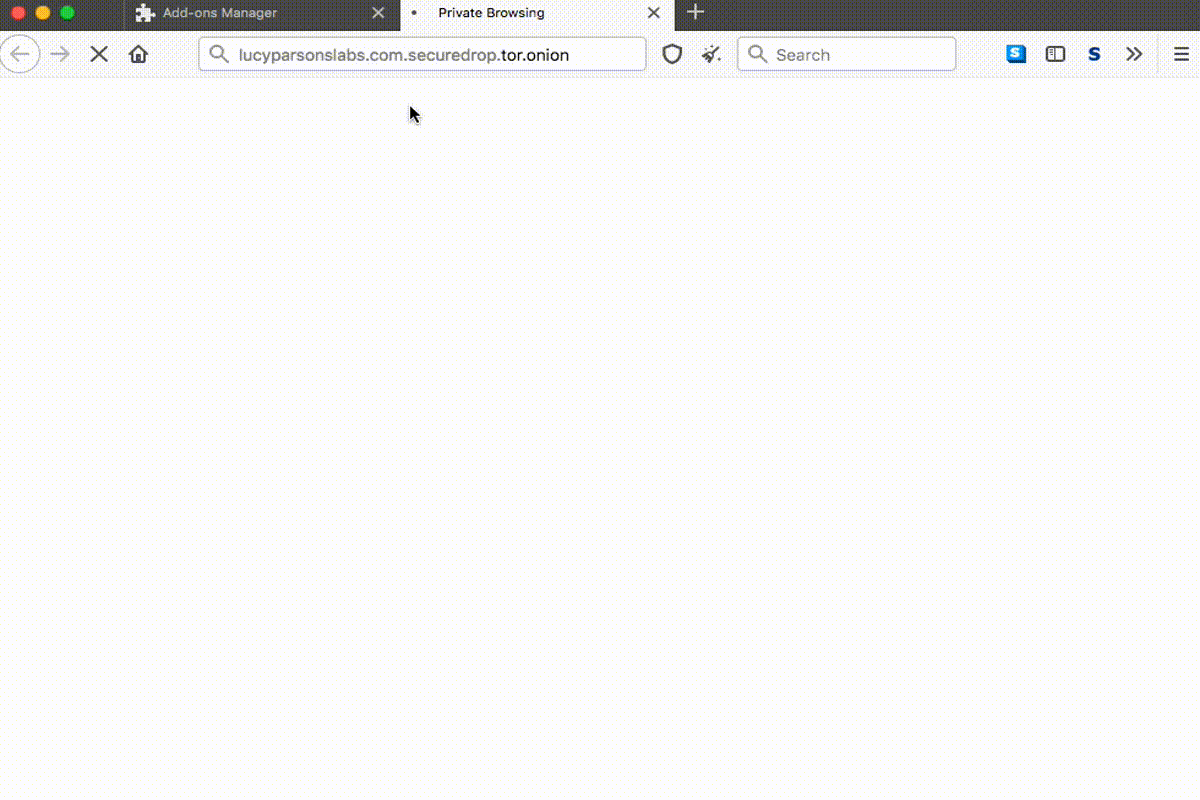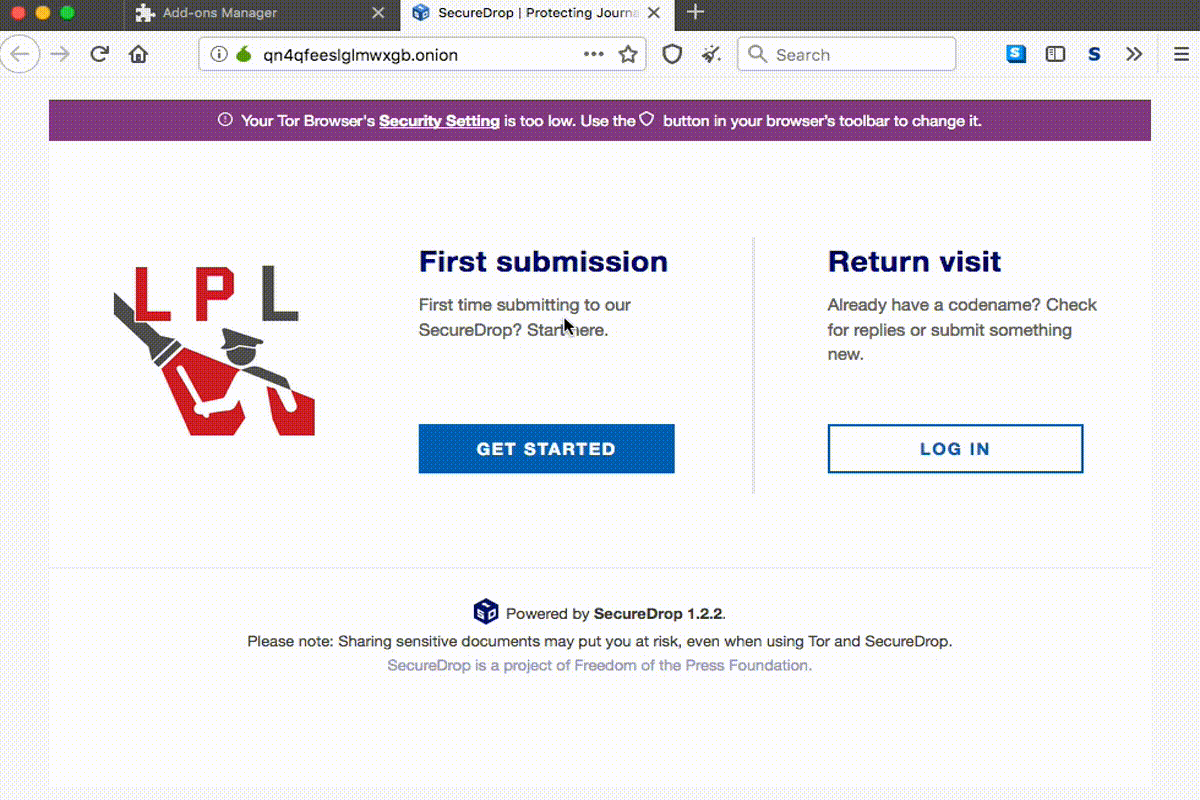
We created a ruleset channel with organizations that opted-in, allowing them to rewrite e.g. lucyparsonslabs.securedrop.tor.onion to the underlying onion URL. Check the repository out if you’re curious to see the logic we use to maintain and update the rules. Our ruleset channel was included in stable Tor Browser beginning with the 9.5 release.